Identity and Access Management (Zero Trust)
Building the bridge between identity, access, and trust
_hero%20banner.jpg?width=2000&height=700&name=Service%20page_Cyber_Identity%20and%20Access%20Management%20(Zero%20Trust)_hero%20banner.jpg)
Zero Trust is a framework for securing infrastructure and data for today's modern digital transformation. Facilitating the development of frameworks of policies and technologies to ensure that the right users (part of the ecosystem within an enterprise) have the appropriate and proportional access to resources as part of a zero-trust model.
Establishing a correct bridge between people, process, and products (technologies), allowing for the management of identities and access to the assets of an enterprise.
_box%20image.jpg?width=1277&height=1277&name=Service%20page_Cyber_Identity%20and%20Access%20Management%20(Zero%20Trust)_box%20image.jpg)
Service overview
Enabling smart access by aligning users, policies, and tools
We understand access is one of the most exploited and abused aspects of security, because it is the portal and it leads to critical assets of the organisation. Access controls need to be applied in a layered defence-in-depth model and, with our understanding, we assist organisations in how to control these exploits and plug the gaps. We guide organisations in exploring access control conceptually and dig into the technologies the industry puts in place to enforce these concepts.
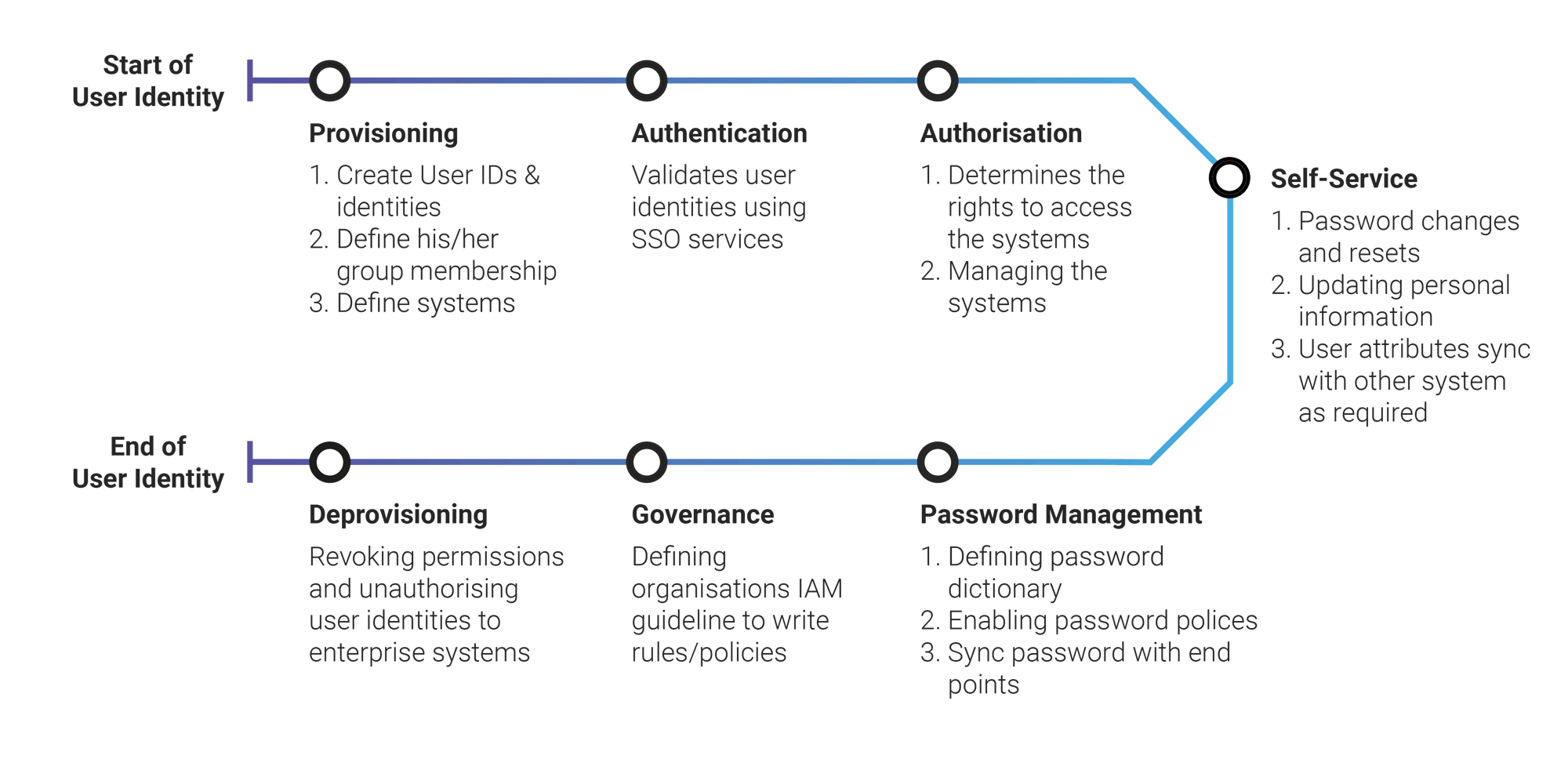
We recognise all the technologies and processes to make up a full enterprise Identity Management (IdM) security architecture design solution, as part of the organisation’s strategic roadmap, which encompass the following key areas:
- User account management
- Auditing and monitoring
- Credential management
- Single sign-on (SSO) functionality
- Access control
- Managing rights and permissions for user accounts
Access isn’t just a doorway - it’s the frontline of your defence. We make sure only the right people get through
- Authentication, authorisation, accountability, and audit
- User management - single sign on, federation
- Central user repository
- Separation of duties and separation of privileges
- Granular polices in a zero-trust model design
- Real-time detection and automation response
- Ensuring “need to know” and “least-privilege” principles are adopted
- Adhering to industry best practice for IdM
- Establishing a consistent user experience across multiple systems/domains
- Enabling a single sign-on, allowing users quick and secure access
- Reducing reliance on remembering multiple complex passwords
- Providing a central encrypted location of audit trails of user actions
- Automation of actions for JML and associated access to resources
- Improved management of user provision and deprovision of resources
- Intrusion detection, intrusion prevention, and information right management systems for unauthorised access
- Pre and post network access verification and validation
Let's start the conversation today!
Our people are here to understand your unique needs and provide tailored solutions. Get in touch with us to kickstart your transformation.


