Security Architecture
Agile security by design

We offer an agile delivery approach that integrates preventive, detective, and corrective measures to strengthen the enterprise security posture.
We design and maintain robust security and technical architectures, including ITHC scoping. Our solutions are tailored to mitigate risks and position security as a business enabler - driving favourable business outcomes.

Service overview
Architecting resilience, mitigating risk
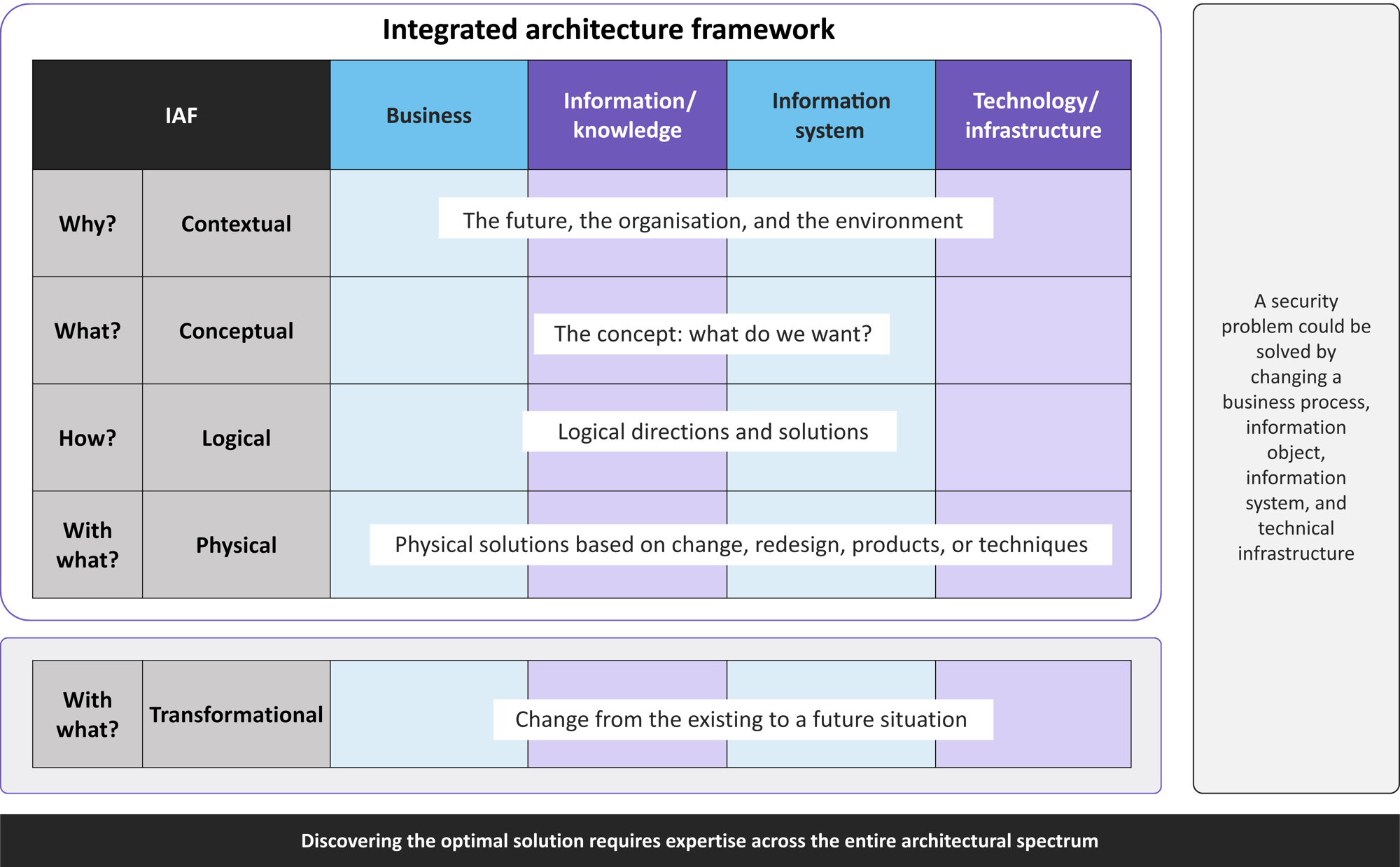
We develop clear designs and reports to provide in-depth security control specifications, using the architecture lifecycle and adhering to NCSC standards consisting of:
- Developing and designing architectures that manage identified risks, using proportionate security controls
- Identification and articulation of risks in conceptual and detailed design of systems and services
- Guidance on how to secure development, build, deployment, operation, and management of systems and services
- Guidance on the adoption and the secure implementation of common architectural blueprints or patterns
- Summary of the technical security analysis in a language that can be
reviewed by different stakeholders - Guidance on how to reduce the likelihood of exploitation of vulnerabilities or impact in the event of a compromise
- Guidance on selecting technologies and solutions by providing adequate mitigation to potential vulnerabilities identified in a system architecture
Designing resilient architectures that secure systems, reduce risk, and enable confident business growth
Features
- Selecting the relevant products, components, and techniques
- Ensuring designs are risk adverse and apply adequate controls
- Designing and implementing fitting architecturural solutions
- Adhering to and incorporating security industry best practice
- Including the core security technologies in the architecture solutions
- Reporting on security vulnerabilities and techniques for defence
- Adherence and compliance with key features of pertinent security architectures
- Designing and developing documented processes
- Developing processes to maintain the security of a system
- Delivered for all security classifications from OFFICIAL to Above-SECRET
Benefits
- Strong security architecture leading to fewer security breaches
- Aiding organisations to identify assets of critical importance
- Proactive security measures, saving on downtime and business impact
- Mitigating disciplinary fines in the event of a breach
- Compliance with key data security standards
- Prevent loss of business confidence, credibility, and trust
- Provides confidence to stakeholders over service security
- Cuts expenses by addressing security concerns proactively during project initiation
- Ensuring security is a business enabler
Ready to transform your organisation?
Let's start the conversation today!
Our people are here to understand your unique needs and provide tailored solutions. Get in touch with us to kickstart your transformation.


